Introduction:
The idea of Internet of Things (IoT) was first discussed in 1982 when a Coca-Cola vending machine was modified at Carnegie Mellon University to report the inventory and the temperature of the loaded drinks making it the first ever IoT appliance. Today IoT devices find their applications in every field be it at home, personal goods, transportation, healthcare, manufacturing, agriculture, military and many more. With the demand for digitalization, the IoT technology is rapidly booming and is currently a $250 billion industry in 2019. While the IoT era of products brings numerous advances and modern comfort to the lives of consumers, the main feature of connectivity of these products create unexpected ports to sensitive data, critical systems and devices. In this article, we will get a basic understanding of the IoT world as well as look into the vulnerabilities and security issues that daunt the IoT devices and discuss some of the possible solutions which can be implemented to overcome these security challenges.
What is IoT?
It is a world of smart sensors and assets connected together to collect and share our data enabling new insights which transform our everyday lifestyle and/or business. The IoT technology is connection of physical and digital components which function without the aid from human mediators. Each component is recognized using its Unique Identifier (UID).
What is an IoT device?
An IoT device is a piece of hardware having sensors that help in transmission of data from one location to another over the internet. The IoT devices comprise of wireless sensors, actuators, computer devices and software which can be embedded within mobile devices, medical devices, industrial equipment and many more.
What is IoT Connectivity?
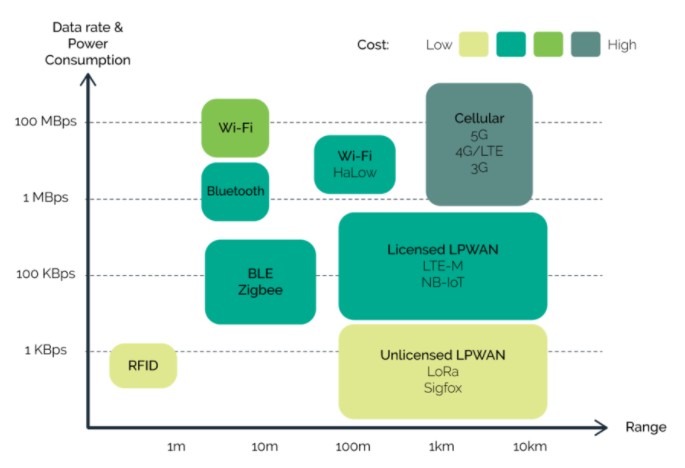
The connectivity in IoT being the vital element is very important. Therefore, selecting the most appropriate connection technology becomes a critical decision for any enterprise. As the IoT devices are developed for wide range of operations, they incorporate connectivity for Wi-Fi, Bluetooth and wired connections (Ethernet cables). Selection of best communication method primarily depends on 3 factors: cost, distance and power consumption.
What are IoT components?
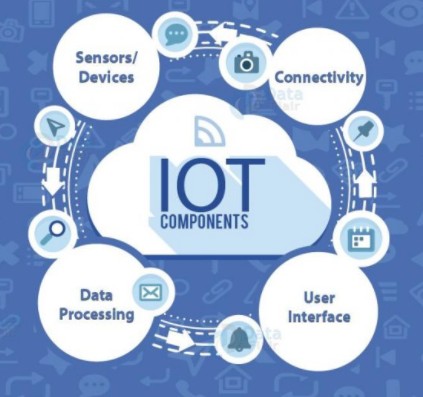
There are a set of components which ensure the working of the IoT technology and are relevant to security analysis of the IoT. The energy and space being major concerns, the IoT devices are composed of limited resources having low computational power and small storage space. Hence, the components are designed to meet these requirements. The key components are:
Sensors/Devices:
The sensors record important parameters of the physical environment like motion, temperature, force, water flow, light, humidity, flame, air quality, proximity and so on. Actuator devices are the ones that affect the physical environment such as producing a sound, turning the light off, opening a door and others. Examples of these devices are TV, speakers, motor and so on.Connectivity:
Now all the data collected by these sensors is first transported to the cloud infrastructure and to other devices from there. The transmission can take place using satellite networks, Wide Area Networks (WAN), Low Power WAN (LP-WAN), Wi-Fi, cellular networks, Bluetooth, etc.Data Processing:
The data collected from the devices then requires processing or in other words taking action based on the data. This can be the simplest task of switching on the room light or in more complex cases of alerting the user of an intruder.User Interface:
Lastly, it’s about how the information is made available to the user either in the form of notifications, beeps, alarms or video feed and various others.
IoT Security:
With the rise in digital transformation amongst industries, organizations and government, the endorsement of IoT technology is rapidly increasing. Study shows in 2018, there were around 7 billion IoT devices installed worldwide, in 2019 the number raised to 26.66 billion. A new IoT device is said to connect to the web every 8 milliseconds estimating the total to 31 billion devices by the end of 2020 and by 2025 to reach an outrageous count of over 75 billion IoT devices. Having so many devices in the market, security becomes the highest concern as most of the data accumulated on these devices are personal and require privacy.
It not just about us interacting with our mobile devices/computers/cars anymore, it’s about the other things that access our devices without our interference. These "things" are continuously communicating with the internet, be it the case of temperature in the house or our heartbeat rate or vehicle sending message to the mechanic to inform about its servicing.
In spite of having undeniable benefits, a 2019 survey showed that "75% of people distrust the way data is shared" whereas "Creepy" was the word used by 63% of people to describe the connected devices. So, increasing the security levels of these devices is a necessity for the companies producing them. The goal is to avoid giving opportunities to intruders/hackers to not only hack into the products but also to the other devices they are connected to.
IoT Vulnerabilities and Security Concerns:
Some of the top security issues are listed below:
IoT manufacturers security negligence:
With all the competition in the market and upgrades available to products, the manufacturers of the IoT devices do not always have security as the critical element in their design process in comparison to adding the internet facilities onto the device. Most of them come with weak, guessable passwords being simple, short and publicly common/available passwords.Data theft:
Since IoT device contains personal information about the user, including credit card details, account passwords, health information, purchase records, etc. An individual can lose their identity if the device is improperly secured and is vulnerable to theft.Lack of physical hardening:
Sometimes the devices can be used for monitoring purposes and will be left at remote locations for long period of time. But these devices can be tampered with physically using a USB with malware, a CCTV camera outside the home can be hacked into if not properly protected.
Data integrity risck in healthcare:
IoT devices in medical industry comprise of heart monitors, pacemakers, defibrillators etc. If not secured adequately, the patient's data can be exploited which will make doctors unintentionally damage the health of their patients. For example, a tampered medial IoT device (pacemaker) can give access to hacker to alter the pacing or deplete the battery.Fraud IoT devices:
With the increase of IoT devices, rogue/counterfeit malicious IoT devices are starting to be installed on secured networks without essential authorization. This device would replace the original device and access all the information the original device would receive. These devices break the network perimeter.Lack of secure updates:
The devices can be sold without having the latest firmware/software update. While updating, the device sends it backup data to the cloud and usually suffers a minor downtime. If the updated files are unprotected or the connection is unencrypted, that could be a source.Threat to others (Botnet attack):
A botnet is a collection of malware infected internet connected devices (millions in count) controlled from a remote location. Hence, it is not a single device affected with malware that poses a threat instead it is the collection of them. The Mirai bot attack in 2016 created a chaos in the IoT security when multiple Distributed Denial of Service (DDoS) attacks infected and brought down the DNS providing services to platforms such as Twitter, Reddit, Airbnb, Netflix and Github.Insecure Network Services:
Consider an unprotected network installed on the devices can be easily infiltrated by the hackers, exposing sensitive user data and financial records to theft. Eavesdropping through the IoT devices is main concern, since a lot of the user information can be jeopardized and used against its owner. In the case of a larger scale of events (industrial level), companies store their large data on the servers which can expose business information to the hackers.Devices with outdated components:
The components play a very critical role for the best functioning of the IoT devices. Components can conveniently be available through open sources and the third-party which weren't scanned for security vulnerabilities.Unprotected device default settings:
Having difficulties to change the default factory settings generates exploits in systems and devices. It is essential to be able to change the default device settings depending on personal preferences.
Methods to improve IoT security:
We discussed several IoT technology security vulnerabilities. Let's look into some of the counter measures on how we can improve on them:
Implementing two separate networks:
Having two separate internet networks connected on their own individual routers is one of the most secure rather more cost-effective solution. This approach keeps our information from being accessed by a compromised device.Thorough device scan:
We must scan our devices for any kind of issues before enabling its connection with the network. To ensure perfect functioning of our devices the scans for vulnerabilities should be scheduled on regular basis.Creating strong passwords:
It very important to access the default settings of the devices and ensure that we replace the default password that the device comes with, to a more unique and secured passwords. Refrain from having the same password for longer time and change it occasionally.
Tracking application permissions on our mobile phones:
Many IoT devices are configurable with our mobile apps on the phone. Usually with agree with all the default privacy permissions while installations of these apps, hence it is very crucial that we read what access we are providing to all these applications running in the background instead of just clicking the "ok"/"agree" button.Having the software/device up to date:
Checking for device updates regularly or better yet having the automatic update option enabled to better enhance the functioning of the device. Most of the times the software updates have fixes for the bugs in the previous version. If our device is more prone to threats, an update might be sent out to fix the issue. So, neglecting the regular software/hardware/operating system updates from the manufacturers exposes our devices to theft.Utilizing Endpoint Detection and Response (EDR) cybersecurity:
The EDR tool system monitors endpoints aggressively for threats, sends alerts during any security breaches and responds whenever possible. IoT components have a complicated security perimeter, meaning more components are connected to the network, the more attackable surface is added to the network.Dedicating IoT to a network:
We can achieve network security by ensuring that all the IoT components are on a separate network where they have the access to the internet required for their operations but not to the corporate network. This wireless network is especially dedicated just for IoT technology, this method is called network segmentation.Changing router default setting:
Enabling the router firewall along with the activation of WPA2 security protocol and using a strong password for Wi-Fi access while disabling the WPS are some measure to ensure the network security.Disabling unnecessary services:
Most of the time we are connected to a lot of devices unintentionally which communicate with the internet without our knowledge. Poorly configured routers can easily be hijacked which have the Universal Plug and Plug (UPnP) option activated. It becomes vital to disable these services when not in use to avoid security accidents.Installing security features in IoT:
Having IoT technology with already enabled high security is complex. Though different researches are in place to use cryptography schemes when designing the IoT system, it is still novel and requires multiple tests to be able to incorporate security given the space and power restrictions of the IoT devices. But installing security features in IoT is the goal, we hope to envision in our future devices.
Conclusion:
The digital transformation has enabled the emergence of IoT at full swing in the recent years. People have become comfortable with having the smart devices which are easily controllable and are embedded in our everyday life, at homes, hospitals, industries, transportation or military. There is no denying that as we have more companies adapting to the digital revolution, there will an increase in the number of installed IoT devices worldwide. As the devices grow in number so does the connectivity, personal data collection and sensitive information collection. IoT security should become a responsibility on personal level, be it for a personal device or network we have access to. With all these advancements, the number of cyber thieves also continues to grow as they have a bigger pool of information to dive into in order to take advantage of the IoT devices for vile reasons. In fact, FBI recommended security measures after several cases of hacking of personal devices. They claimed that our smart TV could get hijacked and the hacker could spy with the help of the built-in camera of the devices whether the device is in use or not. FBI also advices the users of the smart devices to black tape their cameras. Though there have not been any incidents reported, the government thinks precaution is better than cure.
In this article, we discussed the world of IoT, exploring the complete ecosystem comprising of the fundamental components, devices, connectivity with the internet and its security. We dived deeper into the vulnerabilities of security and some crucial drawbacks, which are refraining companies and individuals from adapting to this technology, whose sole purpose is to provide us with a comfortable lifestyle/business. Alongside, we also looked into some of the counter measures to implement in order to avoid any severe damage to either our identity / health or others.
Hopefully, the insight shared in this article will help you make better choices while using the IoT technology as we already know there is no escaping the digitalization era. Lastly, the final question still remains "Internet of Things: Boon or Bane?"
References:
- Internet-of-Things-IoT
- https://www.cs.cmu.edu/~coke/history_long.txt
- http://ird.sut.ac.th/e-journal/Journal/suwimonv/1403739/1403739.pdf
- https://www.mesh-net.co.uk/what-is-the-internet-of-things-iot/
- https://www.arm.com/glossary/iot-devices
- https://securitytoday.com/Articles/2020/01/13/The-IoT-Rundown-for-2020.aspx?Page=1
- https://www.iotsecurityfoundation.org/survey-less-than-10-of-iot-devices-keep-data-secure/
- https://embeddedams.nl/different-ways-to-connect-iot-devices-to-transmit-and-receive-data/
- https://www.edureka.co/blog/iot-applications/
- A. Hameed and A. Alomary, "Security Issues in IoT: A Survey," 2019 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakhier, Bahrain, 2019, pp. 1-5, doi: 10.1109/3ICT.2019.8910320
- https://spectrum.ieee.org/tech-talk/telecom/internet/popular-internet-of-things-forecast-of-50-billion-devices-by-2020-is-outdated
- https://www.internetsociety.org/resources/doc/2019/trust-opportunity-exploring-consumer-attitudes-to-iot/
- https://data-flair.training/blogs/how-iot-works/
- https://www.researchgate.net/publication/325431814_Internet_of_Things_A_Survey_of_Technologies_and_Security_Risks_in_Smart_Home_and_City_Environments
- https://www.intellectsoft.net/blog/biggest-iot-security-issues/
- https://en.wikipedia.org/wiki/Mirai_(malware)
- https://ktar.com/story/2898083/heres-how-to-create-a-separate-network-for-smart-home-devices/
- https://www.trendmicro.com/vinfo/hk-en/security/news/internet-of-things/the-first-steps-in-effective-iot-device-security
- https://www.zdnet.com/article/fbi-recommends-that-you-keep-your-iot-devices-on-a-separate-network/








Raj Vaibhav 4 Jahre
Thanks Honey Pandey. I am a graduate from CMU myself and yet i didn't know about the history of IOT started from CMU. Thanks for recalling this.