Abstract
My dissertation is about the privacy of the IoT devices and their data security. This paper explains about the drastic increase in the use of IoT devices, the amount of data the IoT devices produce on the daily basis, and how this data is used for data analysis to understand consumers needs and buying patterns but also how this data is kept secured by the organizations who develop these devices. As when the word ‘Security’ comes then there is always another word that comes with it that is ‘Breach’, so it is not only about how secured your devices are kept but also how much are they vulnerable to attack the device is. Here it explains some real-life security breach scenarios of how the breach happens or how the user's privacy is violated. The security breaches, data privacy violation is not always done by cyber intruders but also by companies who are owners of these devices.
At the end of this dissertation, it is explained how the privacy breach impacts the consumer, the IoT device developer company, and the third party company connected with any of the device operations. As it is said by Stephane Nappo that “It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it.”
All been said about the data breach there is a lot that companies do to secure IoT devices and the user's privacy. The paper explains different ways organizations secure user's data from cyber intruders and keep them at the bay.
Introduction
The Internet of Things is the term we use for the growing global network of tools and devices that communicate data via the internet. Once IoT devices were used by a handful of organizations like the defense, Manufacturing Plants, etc.. but now there are over 20 Billion IoT devices and these devices are a huge source of the 2.5 quintillion bytes of data we create every day – not just mobile devices, but Smart TV’s, cars, airplanes, Smartwatches,etc.. the internet of things is producing an increasing amount of data.
As such a large amount of data is produced by devices on daily basis then the most important question that comes in mind is about the security of this data. No doubt the companies are securing users data in many ways, but then there are companies who store users data without their permission and is used for various reasons, that is where the privacy is the main concern, as there happen to be lots of cases happened in recent years where there was a data breach from the companies side. If that’s not enough there is always one hacker in a room who is an expert in breaking security. Imagine if any hacker hacks into the Fitbit database who has the data of almost 60 million people and if hacker manipulate the data or manipulate the results of any person how much big problem will it create.
The security and privacy issues in not just limited to the device but it also include the security of the database, servers, other devices connected to the main device, then if company stores IoT data on the cloud then the cloud security, etc.. as it is not always the security breach from the makers of the devices but can also be on part of the data storage party, for example: If there is any company which hires the third party to store its data then it the responsibility of the third party to secure the data as much as of the company who owns the IoT device, I will give all example and real-life example about this kind situation ahead in the paper.
The Internet of Things really makes our lifestyle easy but if its data is not secured properly it will make our life as miserable as it could. It is not just users who get affected by cybercrime but also the organizations that develop these devices and guarantee its security. So some of the questions that IoT developers and consumers need to consider are :
- What personal data does my IoT device collect about others?
- Where is that data sent?
- How is the data used?
- Is all the data collected used, or is there information the device should not collect?
- Does anyone else have access to the data?
- Where is the data ultimately stored?
- How long is the data kept?
- Do we need to build in an expiration time frame for data storage?
- How secure is that data during transfer and storage?
- How will consumers be notified if there is a data breach
How much is IoT Data secured?
In today's world humans are more and more related to technology than they are to other humans for every small thing there is a device this has increased since the innovation of IoT devices and high-speed internet availability and use of IPv 6. Any device that has network connectivity is vulnerable. We use IoT devices to do simple things from turning on the kitchen light to do as big things as using IoT in a Space mission. There are around 20 Billion IoT devices so just imagine how much data is produced, it is calculated that around 2.5 quintillions (2.5 X 1018) bytes of data are produced from IoT devices.
When such huge data is generated the next question comes is about the privacy, as shown in the graph below the top IoT issues are Data Privacy 28% and Increased Security Threats 38%, we can say that when there is a high percentage of security threat to device how can the device be saved in keeping the data secure as all directly related to the security of IoT.
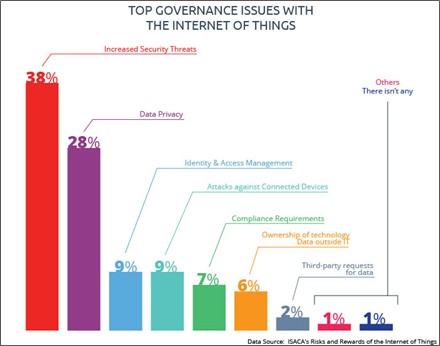
Personal data that is collected by IoT devices is always of value to data hackers and identity thieves.
Real-Life Examples
There are cases in which IoT devices created a huge catastrophe. Some of them are:
- In the UK hackers attacked IoT-connected devices in kitchens across the country, with almost comical outcomes. A smart toaster is forcing consumers into reconsidering eating habits by refusing to toast any bread that isn't considered 'healthy'. Smart Fridges and freezers across the UK are shutting down as soon as the ice cream is detected. (The message is abundantly clear. Leave that white bread on the grocery store counter and stock up on whole wheat, and while you’re there, put down those high-fat/high-calorie frozen goodies in favor of good old wholesome fruit).
- Hackers hacked into the Jeep Cherokee 4x4 vehicle being compromised. Security researchers Charlie Miller and Chris Valasek were able to identify a zero-day exploit which allowed them to send instructions to the vehicle through its entertainment systems. Not only did this provide them the opportunity to remotely change the in-car temperature, they could also influence the vehicle's steering and braking systems. All it required was knowledge of the individual vehicle's IP address to take control.
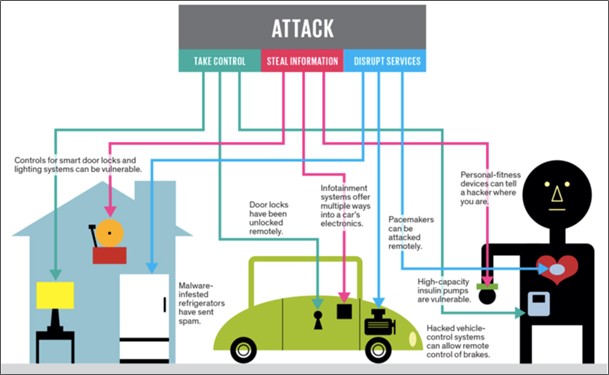
It is not just about the device security that is breached and harmed the users it is also some of the companies which compromise the user's data privacy, that is they stores user's data without their knowledge. Some of the famous cases of such data privacy are:
- According to a CNBC report “In 2019, an Alexa-enabled device recorded a conversation between a husband and wife, then sent it to one of the husband’s phone contacts. But Amazon says that’s because the device accidentally misheard part of the conversation as its wake word, “Alexa,” then misinterpreted other sounds like a series of commands.
According to Amazon's Alexa term of use, Amazon collects most of what you speak to Alexa. That includes any interactions with Alexa, the location of the product that Alexa is running on, and your voice instructions. Specifically, Amazon says it saves these recordings in the cloud until you ask to delete them. But when I checked, it had stored conversations back to March 2016, but I had an Echo since September 2015, so it’s not perfectly consistent. Either way, you should assume that anything you say to Alexa will be stored by Amazon indefinitely. But, understand: Both Amazon’s Alexa privacy FAQ and an Amazon spokesperson says Amazon does not record your conversations all the time, but only when you speak the wake word “Alexa.” In other words, Amazon promises Alexa isn’t always listening to you.”
The data breach of IOT device can lead to huge destruction as nowadays more and more devices are connected to IoT even the heart pacemaker is an IoT if hacked would lead to serious medical condition or death, then Banks uses smart glasses to detect fake checks which if hacked intruder can deposit million dollar check or do any money laundering, there are many such things that create an impact on end-users if data security and privacy are breached.
A solution to keep IoT Device secure
Now their the question arises ‘how to keep data invulnerable?’
Some basic solution that is very common that is to change password at a regular short interval, but it is impossible for many people to remember so many different types of the password so they write down if that written password comes in hands of intruder he will easily harm the device.
Other solutions
In one of the IBM report, it said “IoT devices often have limited computing power and memory capacity, making it difficult to use complex cryptographic algorithms that require more resources than the devices provide. Another challenge is updating IoT devices with regular security fixes and updates. Rolling out security patches to all devices at once can be very difficult in unreliable, low-bandwidth device networks, and many existing security measures, such as web browser security, might not be available to IoT applications.” In addition, security mechanisms might need to be developed or enhanced for new protocols that are designed specifically for the Internet of Things, such as Message Queuing Telemetry Transport (MQTT) and Constrained Application Protocol (CoAP)”
- MQTT protocol is a machine-to-machine (M2M)/"Internet of Things" connectivity protocol, it is designed as an extremely lightweight, publish-subscribe network protocol that transports messages between devices. The protocol usually runs over TCP/IP; however, any network protocol that provides ordered, lossless, bi-directional connections can support MQTT. It is designed for connections with remote locations where a "small code footprint" is required or the network bandwidth is limited.
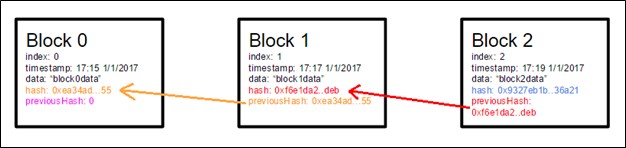
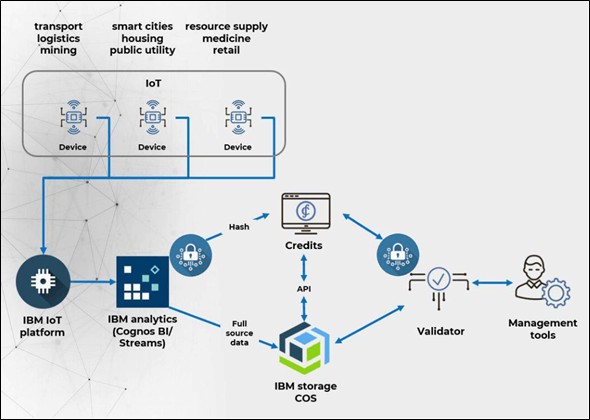
- Then the second solution is Blockchain Technology as this technology uses a block to store the data and each block has two hash on it called as the Previous Hash and Hash, it is on all of its blocks which are connected and form a continuous chain of blocks if anyone even tries to tamper any one of the block's hash and get into it the hacker will get half information and will have to hack in all other blocks and till he/she does it the user will understand that he has been hacked as the hash is 64 characters long and is of 256 bits which to crack in one blocks it would take all the time, so it conclude Blockchain happens to be one of the safest technology use to store your IoT device data save.
Conclusion
To conclude not only IoT devices but any device connected to the network are all vulnerable to attacks unless the security is not considered as the top priority. But we can’t ask people not to use or reduce the use of technology, instead we must make more effort to secure the network links. It is important to secure all devices but, it is important for IoT devices to be secured as IoT applications collect more and more previously unexposed often private, sensitive data and allow access to various control functions over the internet, security becomes a major challenge. So it is important they are more secured and security not only is the responsibility of the company which makes these devices but also lies in the hands of the users.
It is also important for companies to let the user make aware that the company is using their data, for what purposes are they using it? where the data is been send?, How long is the data kept?, How secure the data is during transfer? and whose handling their private data? Companies should notify the user if there is any kind of data breach happened. This all information if not provided or not taken care of can lead to a data breach.
When security is concerned it is important to cover all loopholes. Every device can be attackable until the hackers are there in the world but also that every device is secured until security builders are theirs.
Reference Websites
https://www.cnbc.com/2018/11/19/how-to-delete-amazon-alexa-conversations.html
https://innovationatwork.ieee.org/iot-data-privacy/
https://developer.ibm.com/technologies/iot/articles/iot-trs-secure-iot-solutions1
https://www.iotforall.com/five-reasons-privacy-iot-incompatible/
https://www.linkedin.com/pulse/10-most-terrifying-iot-security-breaches-so-far-you-arent-montgomery/
https://www.embitel.com/blog/embedded-blog/security-challenges-faced-by-iot-based-industries
https://www.information-age.com/iot-privacy-data-insights-four-123485898/
https://www.sumologic.com/blog/iot-data-volume/
https://blog.microfocus.com/how-much-data-is-created-on-the-internet-each-day/